Foreword:
This three-part blog article series focuses on some research work on how to detect effectively Active Directory enumeration in a SOC environment. To help you through this quite long journey, grab a cup of hot beverage of your liking, and use this short reference:
Part 1: about detecting AD enumeration
This first part explains what Active Directory enumeration is, how it is leveraged by adversaries during their offensive operations, and digs into how detecting such activities. It aims at highlighting issues on both efficiency and cost of common detection primitives that detects AD enumeration.
Part 2: AD Canaries & DACL backdoors
This second part will first quickly explain what are DACL backdoors – “An ACE Up the Sleeve” 1 published in 2017 by already famous Specter Ops researchers Andy Robbins, Lee Christensen and Will Schroeder. And will then detail the detection primitive AD Canaries mechanism, along with
some lab implementation and results.
Part 3: Making it useable – improvements and in-production deployment results
This last part will cover some exploratory work that aimed at making this detection primitive useable for SOC operations; improving enrichment and identifying how to effectively exclude on recurrent false positives. It will then analyze results and observations on some in-production deployment we conducted.
Part 3: Making it useable – improvements and in-production deployment results
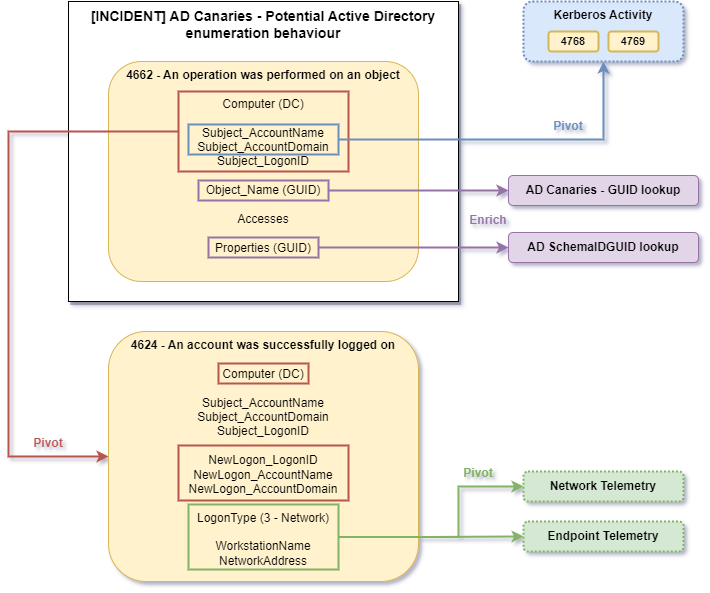
In the previous sections of this blog we covered Active Directory enumeration detection issues and introduced a new primitive for detection: AD Canaries. Analysis of the detection capabilities and requirements indicated that AD Canaries should solve some identified issues for efficient, and low-cost, AD enumeration detection.
Nonetheless, these were only laboratory tests, and no conclusions on the efficiency of this primitive can be done without a proper deployment in production and an assessment in a real environment. This will be our topic for the last section of this blog, focusing on improvements in both detection, investigation and false positive management, and on the result feedback of a deployment in production of AD canaries.
Improvements (and failed attempts) for production viability
As a proper deployment in production would require capabilities to exclude normal behaviors and identify the exact enumeration behavior, some more testing in lab needed to be conducted.
Among those tests, many were unsuccessful attempts to improve the detection primitive. I will not cover all of them in detail, but here are some of these attempts and what I learned from them.
Failed attempt #1: detect specific enumeration through ADCanaries specific attributes
Side note: The first two improvement attempts are failures I faced, and found interesting to share and highlight AD canaries’ limitations and lessons I might have learnt from them. If you do not wish to dig in some arguably bad attempts to improve detection, investigation capabilities or false positive management, you can skip directly to the dedicated section: DACL deployment improvements
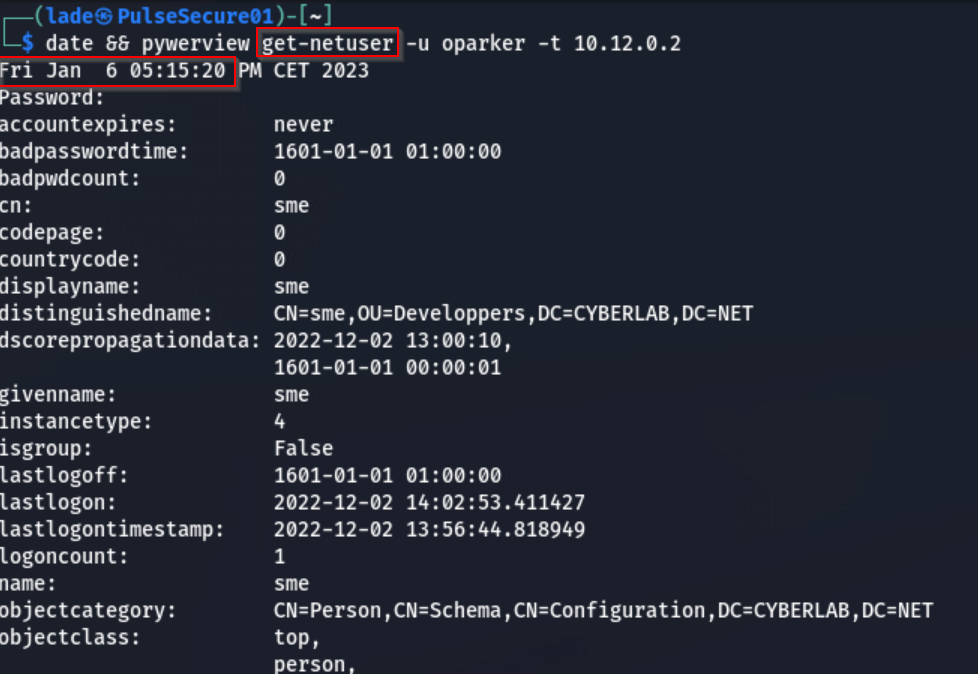
A first approach to identify the exact behavior was to get insights on what attributes were accessed. Similarly to what honeypot accounts would do, I asked myself if it would be possible to deploy specific Canaries with tempting attributes and properties. If so, it would be particularly interesting to design canaries as in Sean Metcalf’s “honeypots accounts”, but detecting specific attempt to enumerate weaknesses in the environment rather than the interaction with the honeypot. The idea here was to design high fidelity AD canaries that would trigger when specific malicious enumeration patterns would be perform to identify known weaknesses. Doing so would probably reduce drastically the number of false positives to face in SOC operations.
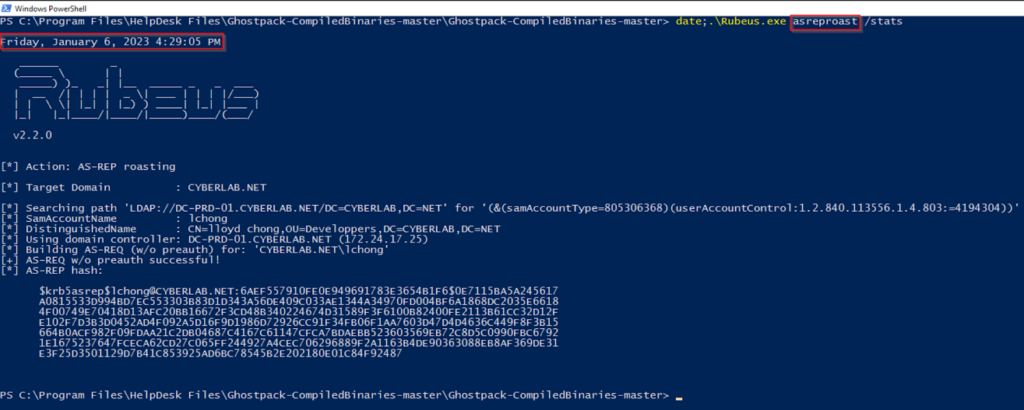
For example, when adversaries perform AS-REP roasting attack to attempt offline password cracking on vulnerable accounts, they can enumerate vulnerable accounts via LDAP. Indeed, accounts that are vulnerable to this attack have the “do not require pre-auth” set in their UserAccountControl attribute. In this case, the question was if deploying a canary configured to be vulnerable to AS-REP roasting (but still hardened by DACL and disabled account) would trigger when enumerating for vulnerable accounts.
Upon testing, I observed that all deployed user canaries would trigger (not just the specifically designed one) upon specific enumeration aiming at identifying AS-REP roastable accounts. This meant something was quite wrong in either the design of the canaries or in my understanding of Active Directory specific enumeration. And it was the latter: I had misunderstood (or forgot) how LDAP filters would match and trigger on accesses on the AD Canary objects.
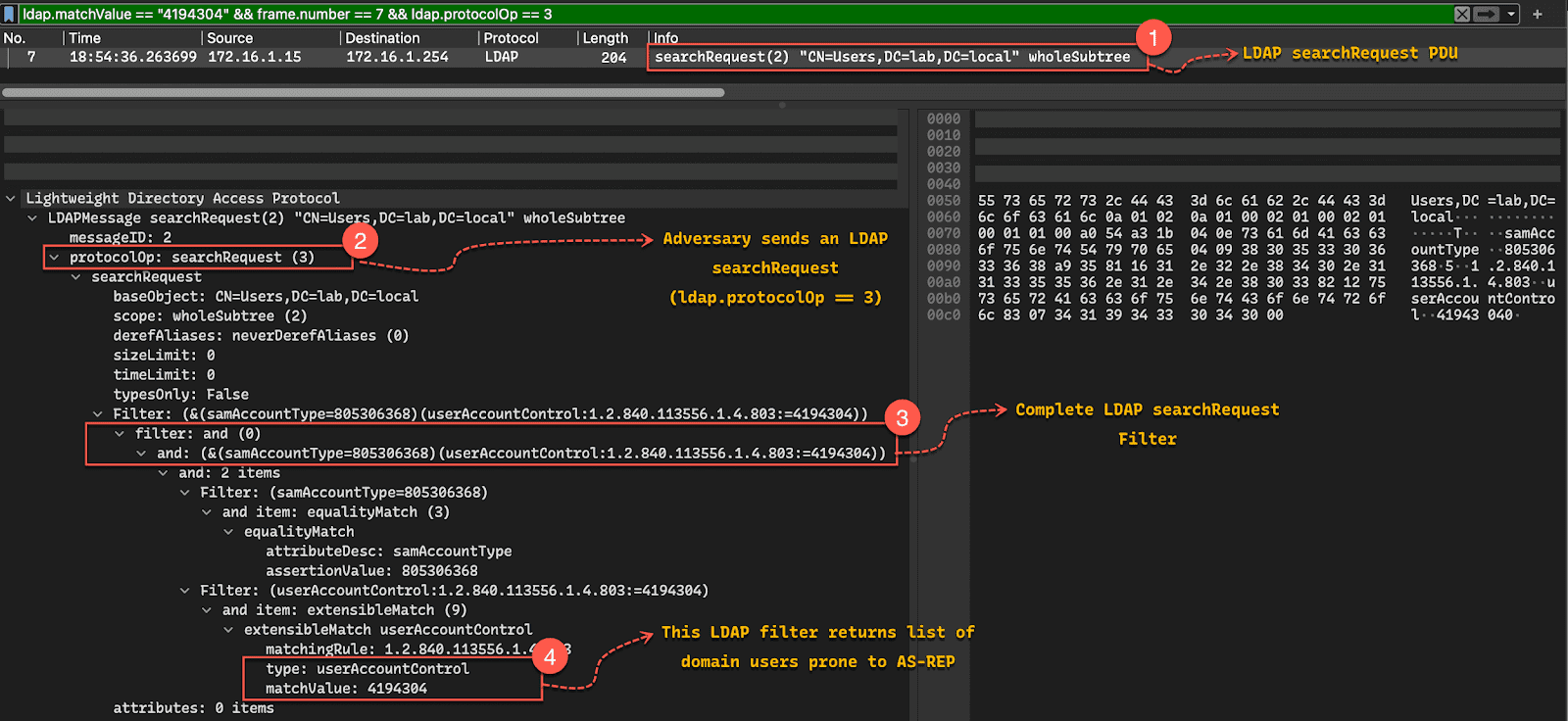 Figure 1 – LDAP request capture in Wireshark from artisanetworks.force.com article
Figure 1 – LDAP request capture in Wireshark from artisanetworks.force.com article
Because LDAP filters apply when accessing the attribute or property of the object – the UserAccountControl in the case of AS-REP roasting – enumeration filters do not matter when using Canaries. Indeed, access to said properties or attributes would always be denied and trigger all ADCanaries whatever the value of their attribute or properties. Which is exactly what was observed when creating such canaries in my lab.
A workaround would have been to design Canaries with specific DENY on those attributes and “regular” ACEs on the rest of the object. However, such object would not be as stealthy as the previous canary version, and impact on AD attack surface would be greater and difficult to assess.
In other words, this was a dead end, but it highlighted some by-design limitations of Active Directory canaries.
Failed attempt #2: ADCanaries matching groups existing within AD
Side note: The first two improvement attempts are failures I faced, and found interesting to share and highlight AD canaries’ limitations and lessons I might have learnt from them. If you do not wish to dig in some arguably bad attempts to improve detection, investigation capabilities or false positive management, you can skip directly to the dedicated section: DACL deployment improvements
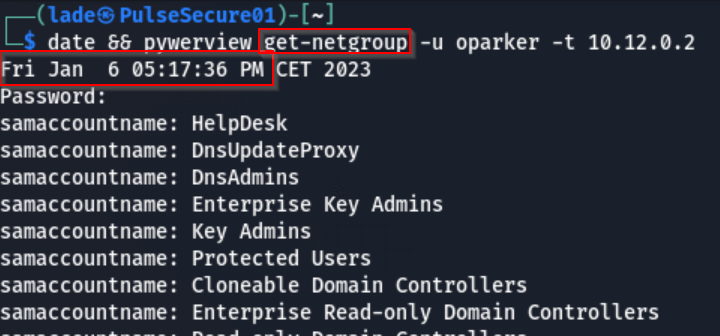
Another failed improvement attempt was the idea of deploying per-ADGroup canary objects, aiming at getting the list of groups that were enumerated. This came during an investigation where we found an adversary using built-in “net” commands to enumerate specific groups in the domain.
This type of targeted enumeration of AD group members would not trigger the default AD canaries as they were only members of “Domain Users” as in the early version of the deployment script. So, I got back head to the grindstone and developed this functionality in the script whenever I could.
This was a bad idea for multiple reasons:
Lowering AD canaries’ stealth capabilities
Adding these canary objects to existing AD groups would allow offensive operators visibility on said objects through the Members property of the group.
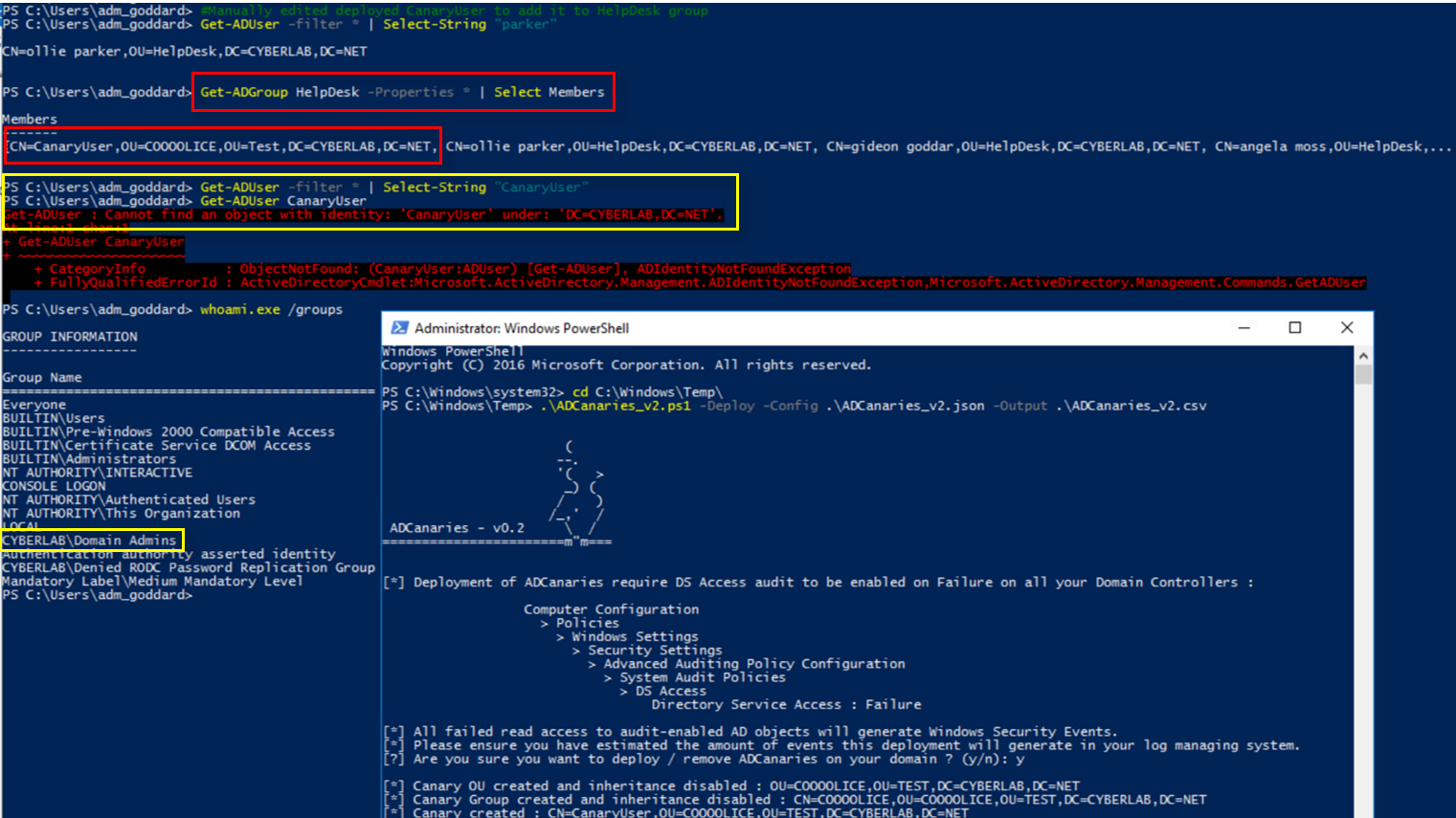 Figure 2 – AD canary added to HelpDesk group – referenced in Members property
Figure 2 – AD canary added to HelpDesk group – referenced in Members property
As we can see here, even from an administrative account the canary cannot be directly accessed, but its distinguished name is still present in the “Members” property of the group it was added to! Giving adversaries opportunities to identify our Canary when doing targeted enumeration.
Lowering effective control on the attack surface induced by AD canaries
Adding the canary objects to existing group would create additional control relationships on the canary object, making it harder to assess the impact on the attack surface of this deployment.
Indeed, by placing AD canaries outside of their isolated bubble we cannot effectively assess that no control relationship misconfiguration will apply to it, nor that the audited deployment will be unaffected by the production environment.
This was one of the more interesting capabilities of AD canaries, an isolated and hardened deployment inside of Active Directory.
Increasing the number of generated events
Increasing the number of canaries and their trigger surface would increase drastically the number of logs generated by this deployment in production. Canaries would also constantly be triggered by any application using LDAP authentication in the environment, as they would be part of existing groups and assets that should be listed quite often.
DACL deployment improvements
You might have noticed in the previous section, I mentioned that AD canary objects were members of the default group “Domain Users” when deployed with the first script version. I discovered that this was due to the default primary group affectation of User and Computer Objects with respectively “Domain Users” and “Domain Computers” groups.
As my previous failure highlighted that having canaries in existing group was not a good idea, it was time to harden the DACLs deployed on these objects and increase their stealth:
- Implementation of full “Hiding the principal” primitive, deploying a dedicated OU for the deployed objects and removing all access to this OU
- Disabling inheritance on the OU and on all deployed objects to limit control relationships over the deployed canaries
- Deploying a dedicated group for canary objects in order to replace the default primary group and remove canaries for all existing groups in the environment
In this final version, the deployment requires only 5 objects to be deployed:
| CanaryOU | The OU deployed to contain all other objects and hide them |
| CanaryGroup | The primary group for user and computer objects, this is the only object that will not be hidden! |
| CanaryUser | A canary object: user account (which is disabled) |
| CanaryComputer | A canary object: computer account (which is disabled) |
| CanaryGroup | A canary object: group |