Introduction to OT Security
Source: CEA list from DIMS event, 16th May 2024
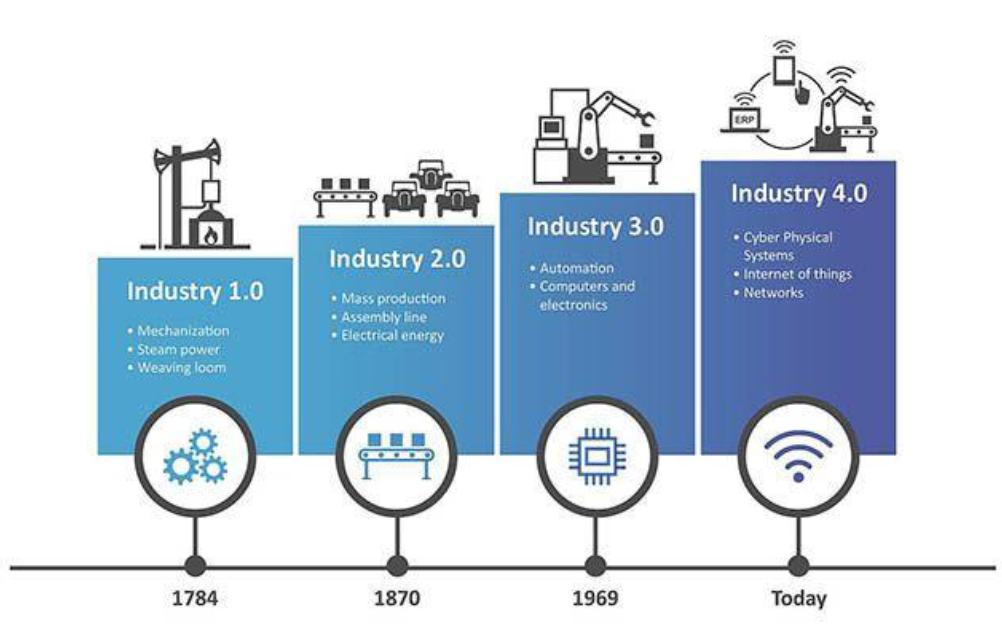
You’ve probably heard of Industry 4.0 – the ongoing automation of manufacturing and industrial practices using modern technology. More industries are embracing this approach by incorporating IoT, cloud, AI and cyber-physical systems into their production chain. The resulting connectivity boosts productivity but brings a need for more robust cybersecurity measures to guarantee systems’ MSC (Maintenance in security condition) and MOC (Maintenance in operational condition).
In this blog, we’ll look at why industrial and manufacturing businesses need to pay closer attention to securing their digital and physical assets.
More connectivity = More opportunities for cybercriminals
Malware, cyber-attacks, ransomware? You’ve probably heard these terms before. But you might not be familiar with the following concepts, which are specific to industrial cybersecurity:
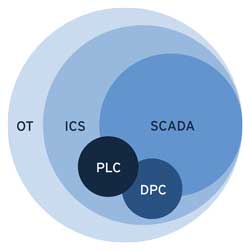
- OT refers to operational technology: This broader term refers to all technologies that support physical operations in industrial, healthcare, building management and transport contexts. OT is an umbrella term that encompasses all technology that interacts with the physical world. In other words, it’s the hardware, software or systems that monitor, control and optimise industrial operations.
- ICS stands for Industrial Control System: ICS falls under the umbrella of OT. This general term describes all the technologies used to automatically manage and monitor an industrial process, for example, in aircraft construction, mining, oil refining or food processing. As the below diagram illustrates, ICS includes the following technologies:
- SCADA: Supervisory Control and Data Acquisition: refers to the organisation of data flows in industry, including:
- PLC: Programmable Logic Controller
- DPC: Discrete Process Control system
- SCADA: Supervisory Control and Data Acquisition: refers to the organisation of data flows in industry, including:
As mentioned above, increasing connectivity in industrial settings has revolutionised manufacturing and operational processes. However, this interconnectedness has also created new vulnerabilities. As a result, industrial businesses are facing an increased risk of cyberattacks targeting critical infrastructure, potentially leading to operational disruptions, data breaches, financial losses and even real-world safety hazards.
Source: https://www.kuppingercole.com/blog/williamson/ot-ics-scada-whats-the-difference
Where is OT in your business?
OT has been around for longer than you might think. Let’s start with a short history lesson!
- The first digital industrial automation systems were controlled solely by isolated controllers, like the first Modicon programmable logic controllers.
- The 1990s saw the birth of industrial connectivity, with the emergence of serial buses such as Profibus to connect controllers, remote I/O and certain data acquisition devices. But these industrial networks were still isolated from other IT systems.
- The next century saw the beginning of convergence between information and operational technologies. Versatile IT equipment, such as TCP/IP protocols, Ethernet cabling or Windows appliances, started to be used in industrial environments. This led to a dramatic increase in connectivity, which exposed traditionally isolated IoT systems to new IT threats.
- Today and in the near future, technologies like cloud computing, 5G or Time-Sensitive Networking will drive other Industry 4.0 trends, such as the Industrial Internet of Things, sensing or augmented reality.
Given the long and complex history of OT, today, many businesses struggle to identify the OT assets within their networks and systems accurately. The increasing convergence of IT and OT environments and the complexity and diversity of OT devices and protocols can make it challenging to map out OT infrastructure comprehensively. This lack of visibility poses significant cybersecurity risks, as unidentified or unmanaged OT assets can become vulnerabilities. Without a clear understanding of their OT landscape, businesses may struggle to implement appropriate security controls, exposing critical systems to potential threats. As such, thoroughly mapping OT assets is crucial.
To understand what exactly constitutes OT in your business, it can be helpful to use the Purdue or PERA model – which you can see illustrated below. This describes a general architecture for industrial control systems and operations. It’s made up of five layers, each fulfilling a specific function.
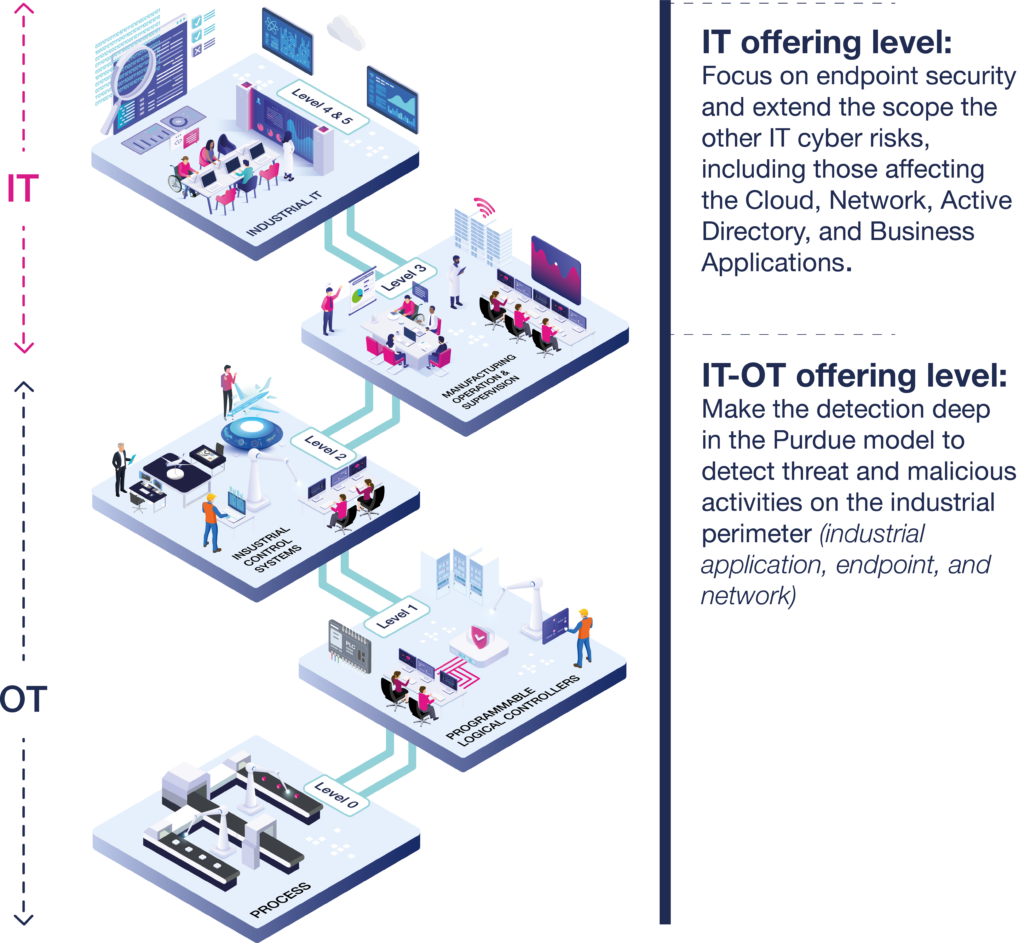
Source: The Purdue model mapped to Airbus Protect’s interpretation
A unified approach to IT and OT security
Once businesses have mapped out all their OT assets, they should look to implement a unified security approach encompassing both IT and OT. A converged security operations centre (SOC) is a great option.
Generally speaking, a SOC gives businesses better visibility into cyber threats. By integrating IT and OT environments, a converged SOC offers the best of both worlds – complete visibility into both systems and networks. This holistic view makes it easier to spot threats that could pass from IT to OT systems, preventing isolated incidents from turning into large-scale attacks.
Linked to this, consistency in security policies and practices across IT and OT environments is a crucial element of any converged SOC. In this way, this model improves risk management and incident response times, and simplifies compliance.
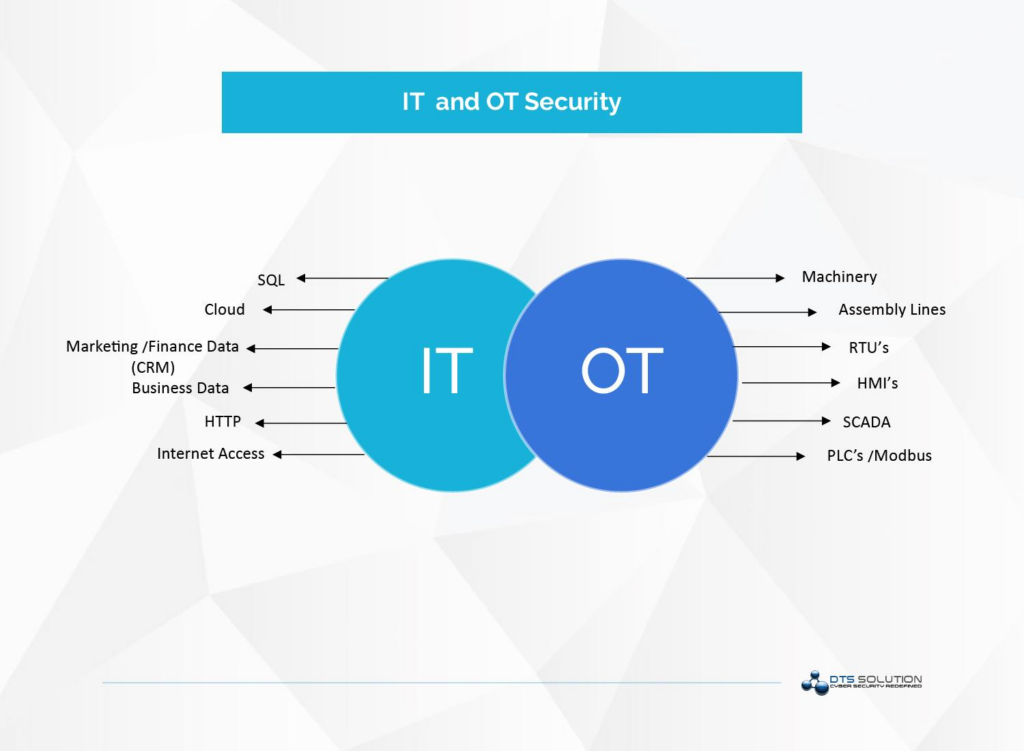
The below chart illustrates the different considerations businesses should take into account when protecting IT and OT assets. They are all typically covered in a converged SOC.
Source: https://www.dts-solution.com/securing-critical-infrastructure-and-protecting-industrial-control-systems-ics-ot-security-series-chapter-1/
Airbus Protect is your OT security partner
Have specific questions about industrial or manufacturing security? We have decades of experience protecting industrial IT and OT. Get in touch to discuss your requirements with our team!
To go deeper with OT and industrial cybersecurity:
Source: https://www.nist.gov/publications/guide-operational-technology-ot-security
Gartner framework: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32022L2555


