 Safety
Safety Safety 101: Understanding operational reliability terminology
MBSA, SMS, ATM… Do you understand all the acronyms in the safety environment? If not, don’t worry. Here’s your guide.
Read more
In cyber-security, we’re notorious for using an abundance of two, three and even four-word acronyms. If you’re new to the space, these can be confusing, to say the least. To make things a little easier, we’ve created this guide! It explains some of the most important terms in the field of incident detection and response, a key area for securing digital corporate assets.
Read on to discover the answers to these questions:
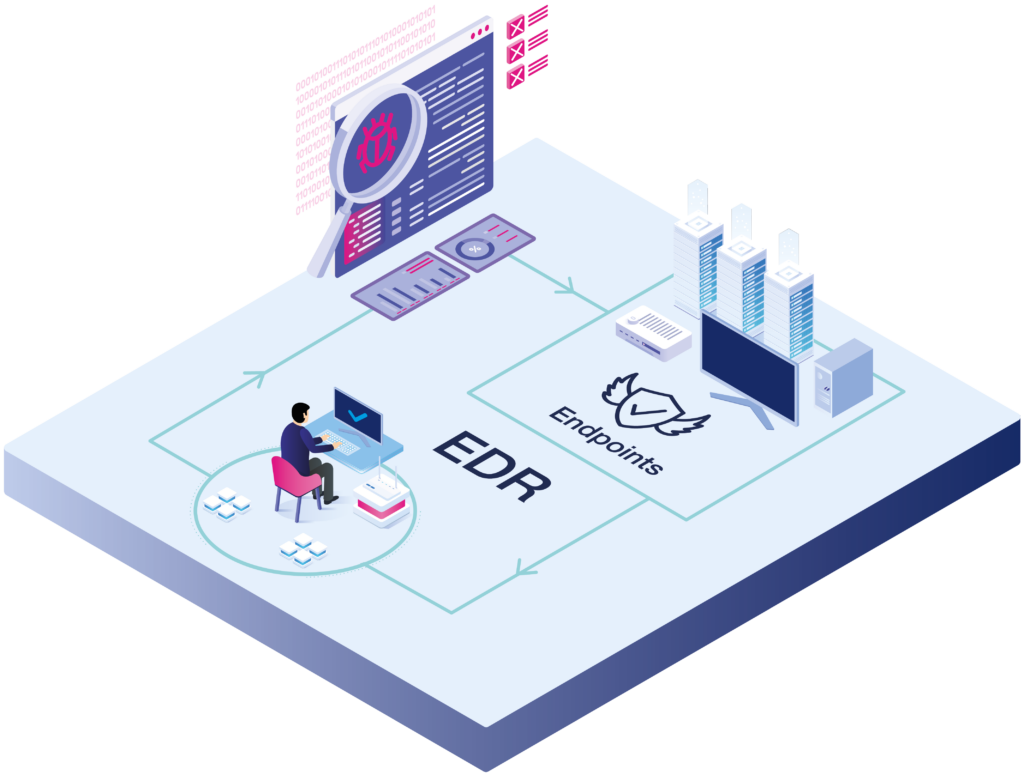
Endpoint detection and response (EDR) is a solution designed to detect and investigate cyber threats on endpoint devices such as PCs, laptops or servers. In contrast to anti-virus software, EDR doesn’t just detect cyber threats by scanning files for virus signatures, but also by looking at the behaviour of endpoint devices. When suspicious behaviour is detected, the tool alerts the IT security team and suggests remediation actions. The EDR tool can also provide automated mitigation responses such as endpoint isolation.
EDR includes:
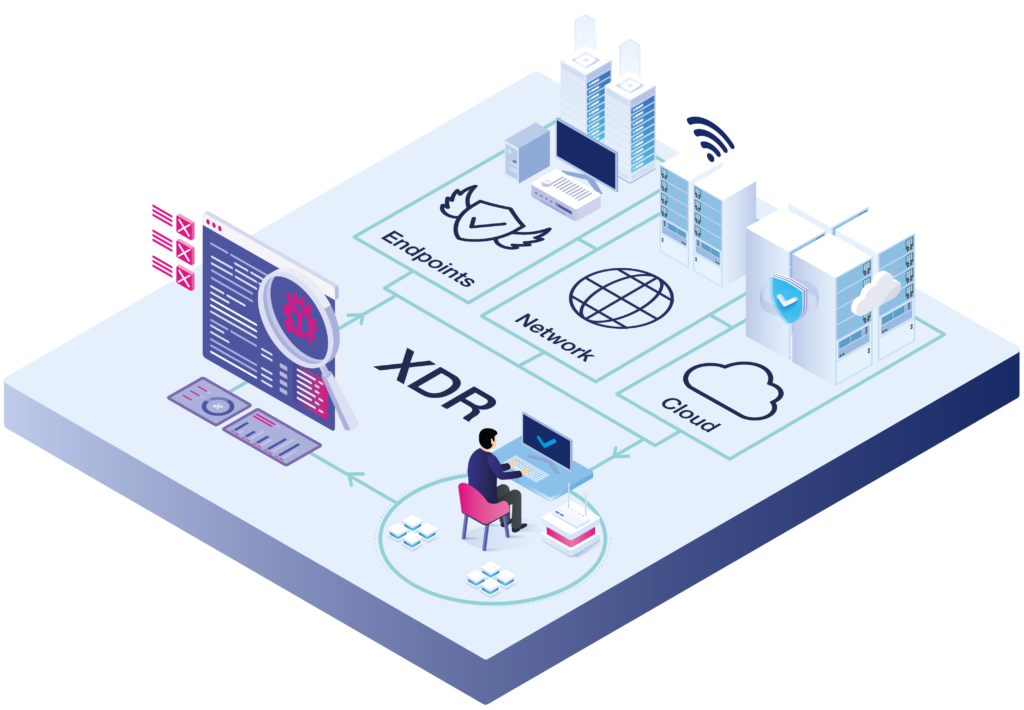
Extended detection and response (XDR) is the evolution of the EDR solution. XDR extends the detection scope beyond endpoints – providing detection, analysis, and response across multiple data sources. XDR collects data and analyses the behaviour of all IT layers and applications. In addition to endpoints, this includes network components and cloud services. This way, XDR creates a holistic view of IT security and possible cyber threats, which simplifies investigation and response activities.
XDR includes:
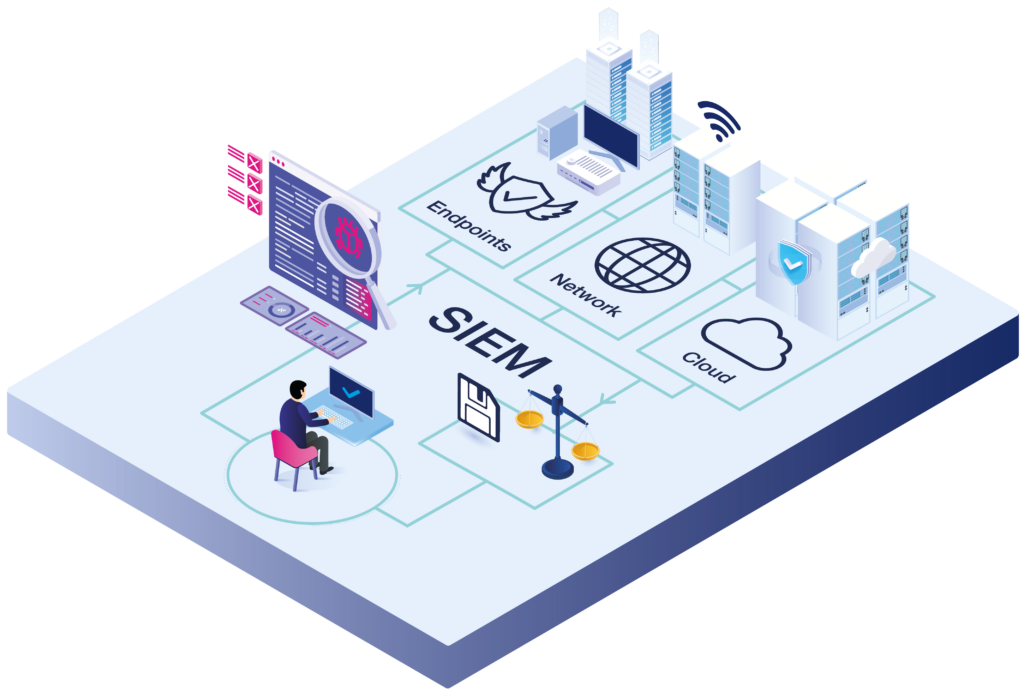
A Security information and event management (SIEM) is a solution that allows organisations to centralise, correlate and analyse data across the IT network to detect security issues. The main capabilities of the SIEM cover log management and centralisation, security event detection, and reporting and search capabilities. It enables analysts to examine log and event data, and also allows them to track and log security data for compliance and audit purposes.
A SIEM solution enables IT security teams to:
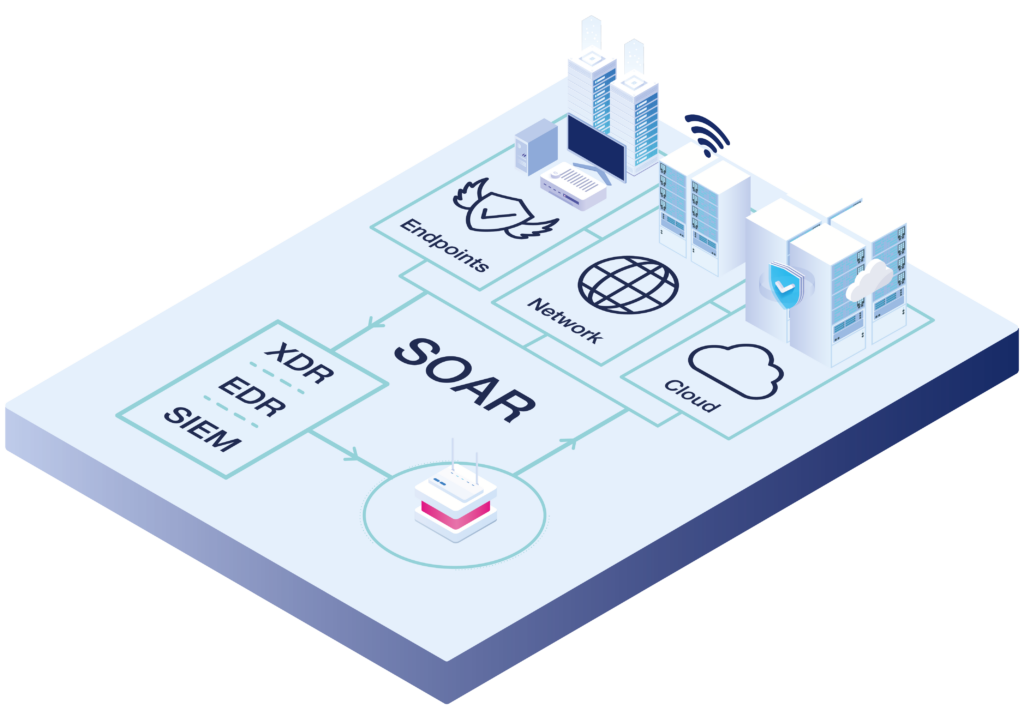
Security orchestration, automation and response (SOAR) is a solution that complements and supports SIEM platforms. SOAR aims to enrich event data, simplify the identification of critical incidents, and automate response actions to specific events or triggers. The aim is to escalate threats only when human intervention is required.
SOAR solutions enable IT security teams to:
Both solutions collect security information from multiple domains. However, their main functions are quite different. SIEM focuses on analysing collected data, detecting threats and alerting. On the other hand, SOAR focuses on generating automated responses to information collected. SIEM solutions are very good at detecting cyber-attacks, but they require manual intervention by security analysts to defend against them. SOAR can work much more independently.
SIEM collects, aggregates, analyses and stores large amounts of log data from various domains. This allows security teams to apply different use cases to the data – including using it for compliance and audit purposes. SIEM solutions require a lot of implementation effort and fine-tuning. They can alert analysts, but don’t include automated response actions.
By contrast, XDR integrates a suite of investigation tools, behavioural analytics and automated remediation into a single platform. Its focus is on advanced threat detection and creating tailored responses. It’s worth noting that XDR doesn’t have the logging, retention or compliance capabilities of a SIEM.
SOAR provides orchestration capabilities that help IT security teams optimise resources and prioritise activities. Typically, the XDR solution has none of these capabilities.
Managed detection and response (MDR) is a service that includes security monitoring and analysis, as well as an element of threat response. Although software is important here, the key to a successful MDR service is having highly skilled analysts on board. This is typically the difference between success and failure.
MDR includes:
The security operations centre (SOC) is a central control centre designed to protect organisations’ IT infrastructure. The SOC is responsible for monitoring security-relevant systems. It also analyses and qualifies threats, as well as initialising and supporting incident response actions. SOC analysts typically work together with cyber-security experts from other areas in coordinated processes using specialised tools.
A typical SOC includes:
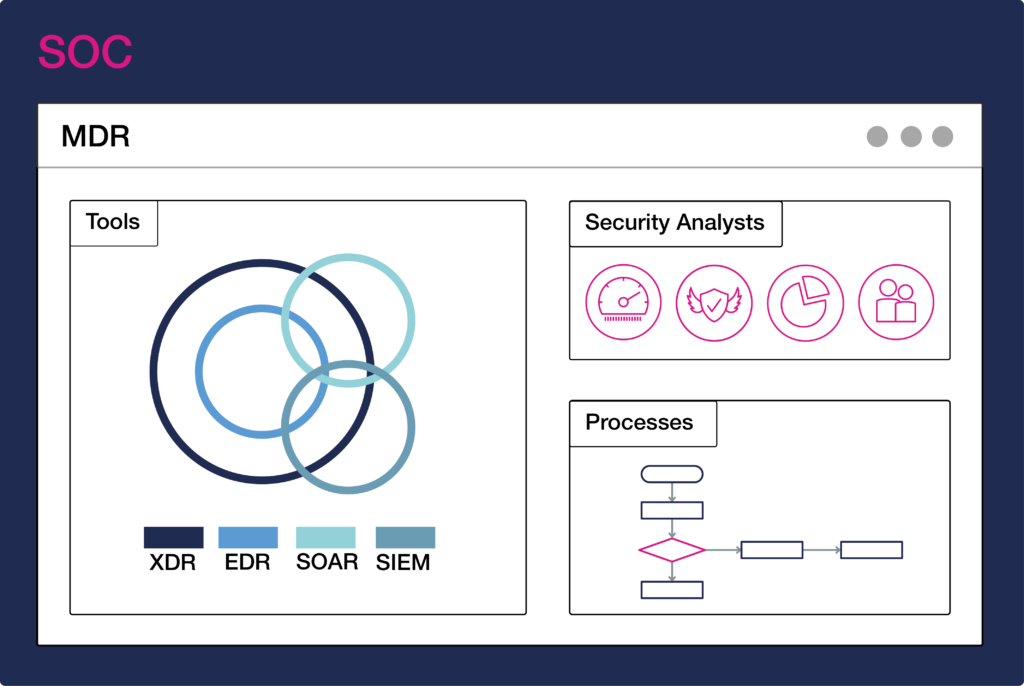
Of course, the above definitions aren’t cut-and-dried. Their features can vary slightly based on different managed security service providers. Often, we see that the tools (EDR, XDR, SIEM, SOAR) have some overlapping features and functionality. But regardless, they need specialised experts to operate them to ensure reliable, efficient results.
Want to learn more about Airbus Protect’s incident detection and response services? We’re here to talk.
 Safety
Safety MBSA, SMS, ATM… Do you understand all the acronyms in the safety environment? If not, don’t worry. Here’s your guide.
Read more Cybersecurity
Cybersecurity Find out how to use CTI as an Operational Support (part 1) Introduction to Cyber Threat Intelligence Cyber Threat Intelligence is a discipline of Intelligence applied to the cyber field. According to Kent’s Analytic Doctrine[1], the role of (Cyber) Intelligence Analysts is to provide “information and insights to policy decision-makers and action-takers”. In the context […]
Read more Cybersecurity
Cybersecurity What is Containerisation? Containerisation – the practice of packaging software code and dependencies into a single ‘container’– has become the backbone of modern, cloud-native app development. Used in conjunction with other technologies like microservices, serverless architectures and DevOps, containerisation enables teams to quickly build, deploy, reconfigure and scale applications to run in any computing environment. […]
Read more