Now that every company is using the cloud, whether it be full cloud, hybrid, or SaaS (Software-as-a-Service), they often worry about being secure and sure that they master their flows and data. You can say that this should have been their concern from the very beginning and maybe before but, as often the way, it has been a secondary consideration.
The expansion of hyperconnectivity leads to an unprecedented surface attack growth with ever-changing attacks based on ransomware, data leakage, and increasingly more complex supply chain attacks. This means cybersecurity providers face never-ending threats, which require a proactive and persistent approach.
With this in mind, cloud security is an important consideration, one that we must consider now to ensure the increasing threats are mitigated. Let’s take a look at cloud security history, make some comparisons with on-premises security, and try to get a view on future trends that we can expect. Spoiler alert: AI is part of it.
How has securing the cloud changed?
Over many years the growth and adoption of cloud technology was stagnant, however along with globalisation, companies increasingly capitalised on technological advancements, and many years later, here we are!
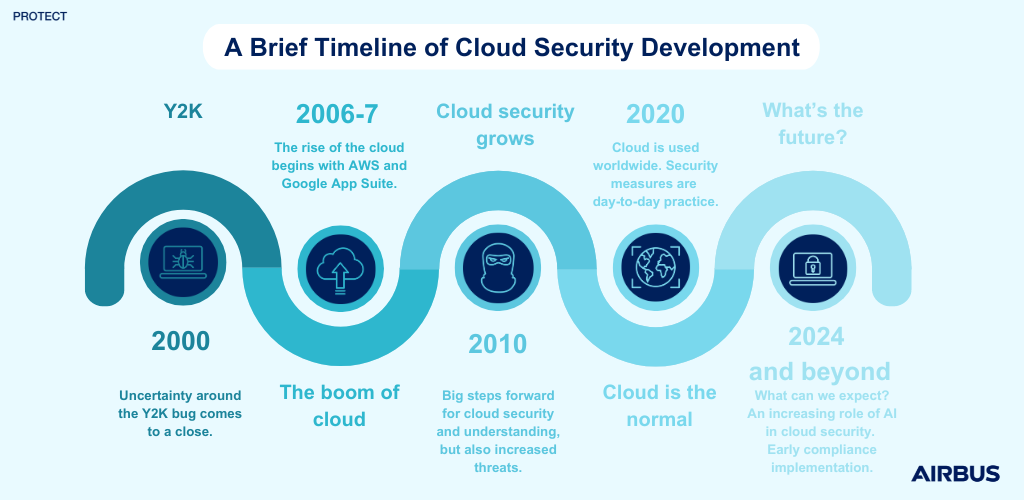
Y2K: the premise
The Y2K bug had the world at a standstill, uncertainty ever lingering in the air. However, when 2000 came around and the world did not end, the world once again started turning; the cloud was now facing slow and gradual growth. We were beginning to see the launch of external cloud services by big companies we know today, such as AWS.
So, what does this mean in terms of security?
In the early 2000s, the cloud was not widely deployed and so specific security concerns that were related to cloud environments were not discussed or understood at the time; there were VPNs between on premises and cloud providers; companies relied on traditional security with firewalls, intrusion detection, and access management; compliance standards were not even a thing then. The few controls companies had on users were made on the cloud provider’s side. Security was not a prime concern.
2010: rise and shine
As we approached 2010, cloud began to take more and more importance. As cloud took the limelight so did the security around it.
On the attackers’ side, it was all about crypto jacking, mining, and gaining access to sensitive data through misconfiguration or credentials theft. By then, cloud providers and companies began to focus on security, better implementation of security controls, and countermeasures. It was also the time of a better cloud understanding, meaning better training for and by cloud admins and cloud-native app builders. This is when the “cloud shared responsibility model” was developed and this meant who was responsible for what, between the cloud provider and users, was now clearer. But way too often, educating the cloud user/admin on the data governance rules and the best practices on secure cloud use was overlooked. Training and awareness sessions were spawning but were as present as they are now.
In the second half of the decade appeared CASBs (Cloud Access Security Brokers), a security enforcement point between cloud users and cloud services. This provided DLP (Data Loss Prevention), proxied connections between on-premises and the cloud, encryption, and compliance rules. This was the first answer to very few efficient controls on LAN (Local Area Network) to cloud data filtering, despite this being the core of the expressed problem. Even if CASBs were protecting the user endpoint from data loss, it was, and still is very hard to prevent sending data to another tenant of the same cloud provider, apart from with a strong CASB added to a dedicated virtual network interface and strong VPC (Virtual Private Cloud) service endpoints. Data tagging also provided a solution, however this was limited as there was no actual defined standard for an “on premises to cloud” compatible metadata format for tagging.
This illustrated the need for strong data governance and classification before any technical measures, even if not fully cloud related. Implementing this can lead to adequate protection means for each data use case, such as, level of encryption, least privilege access, and public/private exposure. In 2014 and 2015, ISO 27017 and 27018 were introduced as best practices. ISO 27017, a standard still used today to support the implementation of ISO27001 information security controls in cloud environments, and ISO 27018, to provide guidance on protecting PII (personally identifiable information) in a public cloud environment, something that became especially prevalent as cloud environments continued scaling up.
2020: opening the highway
Now is the time of maturity and massive usage of cloud solutions and, therefore, securing. Security, compliance, and risk are now a forefront consideration. We have noticed the appearance of CSPM (Cloud Security Posture Management), its derivative CNAPP (Cloud Native Application Protection Platform) and of course the famous and ever-present “Zero Trust” concept, as they represent an important answer to our never-ending security problem.
Cloud security is now based on cloud native security tools, real-time or event-driven management, and incident response, but the law has made its move and now sovereignty is at the centre of the debate. Cloud region enforcement with service control policies are the day-to-day basis of cloud security, with a caveat on no proper sovereign clouds, as most of the providers are US corporate driven. A countermeasure is to encrypt the most sensitive data at rest with on-premises or third-party key management, but this is cumbersome, does not solve the data in use matter, and in the end we are waiting for each cryptographic scheme to be broken.
As it has always been, security is about slowing the attack and, in the end, the principles we were applying on premises are the same for cloud.
How can we face future threats to the cloud?
Looking at the history of cloud, to this day we can see what we have done, what worked well, and what we should have done.
Now if we turn to the future, we can easily imagine that cloud security will rely, as everything, on AI (Artificial Intelligence). This will consist in low noise detection (Machine Learning) and applying compliance policies from the very beginning (design level) with NL/LLM (Natural Language/Large Language Model). As on premises, this will help for fast decisions on remediation and adaptability for discovering threats.
We can also imagine that AI will help on automatic cloud data scanning to detect forbidden patterns such as PII (Personal Identified Information), PHI (Personal Health Information), Secrets (access keys, passwords) and keyword-based documents (e.g. AWS Macie for S3 scanning), with the trade-off of having to trust the cloud provider with automatic data reading permissions. If we consider this, we may start seeing more companies, particularly those dealing with sensitive data, using their own private cloud to face this changing environment. Or, alternatively, this pattern may be a slow and gradual change as we have seen historically and in the nearer future we may see the current pattern continue and a more stringent approach to security may take precedence. Whatever the case, companies must consider their position to be prepared.
And, maybe if we look a little bit further, 6G for example, on-premises, and cloud will certainly be old patterns and hybridation the standard. So securing will be all based on endpoint protection and zero trust for every single application and data usage. Can’t wait to see that.
When we look back at the history of cloud security we can pretty much see a repeating pattern throughout the cyber realm. One which often leaves those who follow it, in a non-optimal position. Companies flow with this until, suddenly, they no longer can and face increased risk and threats which they respond to. In order for cloud security to move in the right direction, companies need to take a proactive stance and be future ready!


